Today’s digital ecosystem is interconnected, and APIS (Application Programming Interfaces) are the backbone of applications of all types, whether web or mobile. The most common type of API architecture is Representational State Transfer (REST) APIs, which allow smooth communication between the client and server.
Nevertheless, REST API security has become one of the most critical aspects of creating a web app due to the growing dependence on REST APIS. The 2026 State of API Security Report by Traceable AI highlights these challenges, revealing that 57% of organizations have suffered API-related breaches in the past two years, with many experiencing multiple incidents.
In 2026, securing REST APIS is more vital than ever before, not just to protect sensitive information but also to maintain the integrity and trustworthiness of a web application as a whole.
Why REST API Security is Crucial in 2026
By 2026, an increasing number of organisations will shift their operations and services to the online world, and APIs will be a focal point of data sharing for these organisations. As with any other API, security for REST APIS is essential to prevent attacks that could lead to breaches, data leaks, or even system downtime.
The tremendously rapid rise of cyber threats and vulnerabilities has made it critically important for developers, businesses, and consumers alike to secure APIS against unauthorized access and exploitation.
It’s time to dig down the hill to understand the reasons why REST API security is necessary for your web app in 2026.
Rise of Cybersecurity Threats:
An increase in cybersecurity threats primarily occurs as hackers enhance their skills in technological attacks. Due to the large amounts of sensitive data being processed, REST APIs make prime targets for cybercriminals. The damage from API breaches can be very significant, including data loss, identity theft, or even complete system compromise. These evolving threats will make API security that much more critical in 2026.
API Security is Integral to Web App Security:
Web app security depends heavily on REST API security, as client-server interactions rely on it. Vulnerable APIs can expose the entire app to attacks, leading to major risks for reputation, privacy, and functionality.
Growing Demand for AI and IoT Integration:
The Demand is increasing for AI and IoT integration. The increasing innovations in artificial intelligence (AI) and the Internet of Things (IoT) worldwide, across various industries, are driving the need for centralized security for REST APIs in AI development, as well as IoT integrations.
Data exchange between devices, sensors, and cloud-based AI algorithms takes place through APIs, and since they form the highways for the compromise threat, the security of APIs never goes in vain.
Best Practices for REST API Security in 2026
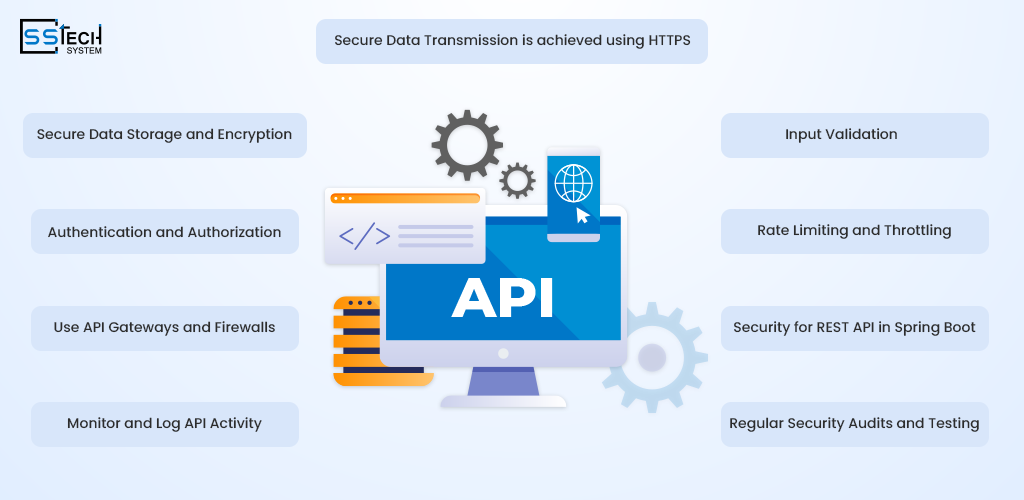
In 2026 developers are expected to secure REST APIs by following best practices and ensuring this at all stages of the API lifecycle. The key strategies for securing REST APIs are as follows.
Authentication and Authorization
Authentication confirms whether the user or client attempting to access the API is authorized, and authorization defines what the user can do. Some REST API users’ authentication methods are:
- OAuth 2.0: API authorization using OAuth 2.0 is a well-established standard, particularly for third-party applications.
- JWT (JSON Web Tokens): A compact and secure method for transmitting user identity information between client and server.
- API Keys: Identifiers used as a unique key to access the API with the help of other authentication methods.
Node.js secure API development is often built using OAuth and JWT, protecting access to critical systems resources to be accessed by authorized users only.
Secure Data Transmission is achieved using HTTPS
Using HTTPS encrypts data between client and server, protecting it from interception or tampering. REST APIs without HTTPS are vulnerable to man-in-the-middle (MITM) attacks. By 2026, securing REST APIs will require HTTPS across all web, mobile, and IoT platforms.
Rate Limiting and Throttling
Since the use of the REST API is essential, yesterday’s exercise focused on implementing rate limiting and throttling, as we cannot allow the API to be abused and, as a result, it cannot be subjected to denial–of–service attacks.
Rate limiting prevents clients from making more than a specified number of requests within a specific time frame. In contrast, throttling slows down the API whenever the demand for requests exceeds a certain threshold. These protect your APIs from malicious traffic that overwhelms them.
Input Validation
Proper input validation ensures data is safe and in the correct format. Use tools like OWASP ZAP or Burp Suite to detect vulnerabilities. Sanitizing inputs helps protect APIs from SQL injection, XSS, and other threats.
Secure Data Storage and Encryption
Data kept in plaintext should never be considered sensitive. Sensitive information must be protected both at rest and in transit, and developers should utilize encryption algorithms. This refers to the encryption of API keys, tokens, and any other personal data stored on the server.
Protect REST APIs in mobile apps (iOS and Android) by encrypting data, placing it in a secure container, and adhering to platform-specific security practices.
Use API Gateways and Firewalls
An API Gateway is a proxy between clients and servers that offers supplementary security layers, enforcing traffic by validating requests. Malicious requests made to your API can be prevented from reaching it by using API firewalls, which filter out unwanted traffic and block known attack patterns. These tools supplement the security provided by the REST API against various threats.
Security for REST API in Spring Boot
If you’re then developing your API in Java, you can use Spring Boot — a famous Java framework — and Spring Security. A powerful toolkit, Spring Security offers seamless integration of OAuth, JWT, and other authentication methods, making it essential for securing Java REST APIs in 2026.
Regular Security Audits and Testing
Tools like Postman, Insomnia, and Swagger automate REST API security testing, helping identify vulnerabilities efficiently. Regular penetration testing and vulnerability assessments are essential to keep APIs secure against evolving threats.
Monitor and Log API Activity
Continuous monitoring of API activity is vital. Detailed logging of requests and responses helps developers quickly spot security incidents and act fast. Tools like the ELK Stack (Elasticsearch, Logstash, Kibana) are often used for this purpose.
REST API Security Solutions by SSTech System
By 2026, you will need to secure REST APIs to protect sensitive data and ensure the integrity of web and mobile applications. SSTech System offers a wide range of REST API security solutions, detection, and prevention of emerging threats to your Business, allowing you to secure your APIs and applications. They provide services from the development to the deployment and then continue to monitor the API throughout its lifetime.
REST API security has the following key features:
- Authentication & Authorization: Using industry standard abstraction of the authentication and authorization layer, such as OAuth 2.0 and JWT (JSON Web Tokens), making sure that only the authorized user can access API resources.
- Rate Limiting & Throttling: It includes protecting APIs from denial-of-service (DoS) attacks by limiting the request rate so that excessive requests from a single host do not deny request processing opportunities to other hosts.
- Data Encryption: It protects sensitive information from interception, both in transit (using HTTPS) and at rest.
- Continuous Monitoring & Incident Response: Automated and continuous tracking and response to immediately notice and prevent security threats as they happen.
Conclusion
With the rising importance of REST API security, developers must follow best practices to maintain secure APIs and establish consistent trust with users. By 2026, REST APIs need to be secured, not optional. The process of secure REST API development is a labor-intensive one, as every step from start to finish is essential for your API’s integrity and protection.
Frequently Asked Questions
While HTTPS is vital in that respect, it does not suffice on its own. Additionally, you should implement authentication, authorization, input validation, and other security measures to thoroughly protect the application.
Regular vulnerability assessments are advised after any changes to the API or its infrastructure. Continuous use of automated testing tools is expected, with manual testing conducted at intervals of no less than quarterly.
OAuth is an authorization framework that enables third-party applications to access resources owned by a resource owner. A JSON Web Token (JWT) is a compact and secure means of transmitting information between parties.